Hello guys, if you are preparing for Cyber Security Engineer Job interviews and looking for frequently asked Cyber Security Interview questions with answers then you have come to the right place. Earlier, I hare shared best Cyber Security online courses and best Ethical Hacking online courses and in this article, I am going to share 20 common Interview Questions for Cyber Security Professionals. These interview questions are great to revise key Cyber Security concepts, tools, and process before you go for any interview.
Cyber security is a very critical area that people are involved with in one way or the other on daily basis. If an employer in this particular field wants to hire someone, they will look for a more competent person who will serve them with the best and nothing less.
Therefore, for you to be that competent person, you have to be equipped with all the answers that the interview panel will need. Don’t worry because the right answers for the questions that you will be asked are as follows.
Though, its not very comprehensive and may not cover every aspect of Cyber Security. If you think a topic is missed, feel free to suggest in the comment and I will try to add more questions. You can also contribute Cyber security questions asked to you during interviews to give others an idea about depth and difficulty level of questions on different companies.
Therefore, for you to be that competent person, you have to be equipped with all the answers that the interview panel will need. Don’t worry because the right answers for the questions that you will be asked are as follows.
Though, its not very comprehensive and may not cover every aspect of Cyber Security. If you think a topic is missed, feel free to suggest in the comment and I will try to add more questions. You can also contribute Cyber security questions asked to you during interviews to give others an idea about depth and difficulty level of questions on different companies.
20 Cyber Security Interview Questions with Answers
Without wasting anymore of your time, here is the list of 20 Cyber Security Interview Questions with answers. You can use these questions to revise key Cyber Security concepts in quick time before your interview.
1. What are the differences between Asymmetric and Symmetric encryption?
Answer:
2. What is CIA triad?
Answer: this is a mode that is designed to guide policies for information security. CIA stands for Confidentiality, Integrity, and Availability
3. What are the elements of Cyber security?
Answer:
4. What are the advantages of cyber security?
Answer:
5. What are the different layers of the OSI model?
Answer: there are seven different layers of OSI model which are as follows:
6. What is Spyware?
Answer: Spyware is a malware that aims to steal data about the organization or person.
7. What are the steps to secure web server?
Answer:
8. What are the types of sniffing attacks?
Answer:
9. What are the various methods of session hijacking?
Answer: the following are various methods of session hijacking:
10. What is cybersecurity?
Answer: Cybersecurity refers to the protection of hardware, software, and data from attackers. The primary purpose of cyber security is to protect against cyber attacks like accessing, changing, or destroying sensitive information.
11. Explain vulnerabilities in network security.
Answer: Vulnerabilities refer to the weak point in software code which can be exploited by a threat actor. They are most commonly found in an application like SaaS (Software as a service) software.
12. Explain the main difference between Diffie-Hellman and RSA.
Answer: Diffie-Hellman is a protocol used while exchanging key between two parties while RSA is an algorithm that works on the basis two keys called private and public key.
13. What is Forward Secrecy?
Answer: Forward Secrecy is a security measure that ensures the integrity of unique session key in event that long term key is compromised.
14. What is a security auditing?
Answer: Security auditing is an internal inspection of applications and operating systems for security flaws. An audit can also be done via line by line inspection of code.
15. What is the importance of penetration testing in an enterprise?
Answer: Here are two common application of Penetration testing.
16. What are the disadvantages of penetration testing?
Answer: Disadvantages of penetration testing are:
17. What are the examples of non-physical threats?
Answer: Following are some examples of non-physical threat:
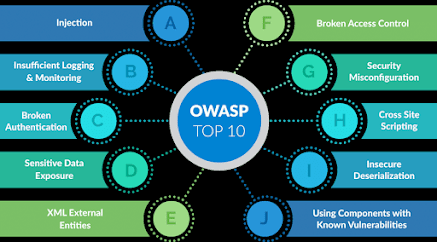
18. What are security vulnerabilities as per Open Web Application Security Project (OWASP)?
Answer: Security vulnerabilities as per open web application security project are as follows:
19. What is the use of a firewall and how it can be implemented?
Answer: A firewall is a security system used to control and monitor network traffic. It is used for protecting the system/network from malware, viruses, worms, etc., and secures unauthorized access from a private network. The steps required to set up and configure the firewall are listed below:
20. How can you prevent CSRF attacks?
Answer: CSRF is referred to as Cross-site Request Forgery, where an attacker tricks a victim into performing actions on their behalf. CSRF attacks can be prevented by using the following ways:
As of now, you must have now seen what the questions that are commonly asked look like. They are the right questions for you in this journey and therefore you have to consider yourself lucky because you have found the real deal. You are surely going to walk into the interview with great confidence and you will eventually make it on that big day.
1. What are the differences between Asymmetric and Symmetric encryption?
Answer:
|
Asymmetric encryption |
Symmetric encryption |
|
Different keys for encryption & decryption |
Same key for encryption & decryption |
|
Is slow |
Is fast |
|
Most of the times used for securely exchanging secret keys |
Used for bulk data transmission |
2. What is CIA triad?
Answer: this is a mode that is designed to guide policies for information security. CIA stands for Confidentiality, Integrity, and Availability
3. What are the elements of Cyber security?
Answer:
- Application security
- Information security
- Business continuity planning
- Network security
- Operational security
- End-user education
4. What are the advantages of cyber security?
Answer:
- It protects the end-users.
- It prevents unauthorized users.
- It increases recovery time after a breach has occurred.
- Enhances good protection for data and networks.
5. What are the different layers of the OSI model?
Answer: there are seven different layers of OSI model which are as follows:
- Network Layer
- Physical Layer
- Application Layer
- Transport Layer
- Data Link Layer
- Session Layer
- Presentation Layer
6. What is Spyware?
Answer: Spyware is a malware that aims to steal data about the organization or person.
7. What are the steps to secure web server?
Answer:
- Update ownership of file.
- Keep your web server updated.
- Disable extra modules in the web server.
- Delete default scripts.
8. What are the types of sniffing attacks?
Answer:
- LAN sniffing
- Protocol sniffing
- ARP sniffing
- Web password sniffing
- TCP Session stealing
- Application-level sniffing
9. What are the various methods of session hijacking?
Answer: the following are various methods of session hijacking:
- IP Spoofing
- Using packet sniffers
- Blind Attack
- Cross-Site Scripting (XSS Attack)
10. What is cybersecurity?
Answer: Cybersecurity refers to the protection of hardware, software, and data from attackers. The primary purpose of cyber security is to protect against cyber attacks like accessing, changing, or destroying sensitive information.
11. Explain vulnerabilities in network security.
Answer: Vulnerabilities refer to the weak point in software code which can be exploited by a threat actor. They are most commonly found in an application like SaaS (Software as a service) software.
12. Explain the main difference between Diffie-Hellman and RSA.
Answer: Diffie-Hellman is a protocol used while exchanging key between two parties while RSA is an algorithm that works on the basis two keys called private and public key.
13. What is Forward Secrecy?
Answer: Forward Secrecy is a security measure that ensures the integrity of unique session key in event that long term key is compromised.
14. What is a security auditing?
Answer: Security auditing is an internal inspection of applications and operating systems for security flaws. An audit can also be done via line by line inspection of code.
15. What is the importance of penetration testing in an enterprise?
Answer: Here are two common application of Penetration testing.
- Financial sectors like stock trading exchanges, investment banking, want their data to be secured, and penetration testing is essential to ensure security.
- In case if the software system is already hacked and the organization would like to determine whether any threats are still present in the system to avoid future hacks.
16. What are the disadvantages of penetration testing?
Answer: Disadvantages of penetration testing are:
- Penetration testing cannot find all vulnerabilities in the system.
- There are limitations of time, budget, scope, skills of penetration testers.
- Data loss and corruption
- Down Time is high which increase costs
17. What are the examples of non-physical threats?
Answer: Following are some examples of non-physical threat:
- Loss of sensitive information
- Loss or corruption of system data
- Cyber security Breaches
- Disrupt business operations that rely on computer systems
- Illegal monitoring of activities on computer systems
18. What are security vulnerabilities as per Open Web Application Security Project (OWASP)?
Answer: Security vulnerabilities as per open web application security project are as follows:
- SQL Injection
- Cross-site request forgery
- Insecure cryptographic storage
- Broken authentication and session management
- Insufficient transport layer protection
- Invalidated redirects and forwards
- Failure to restrict URL access
19. What is the use of a firewall and how it can be implemented?
Answer: A firewall is a security system used to control and monitor network traffic. It is used for protecting the system/network from malware, viruses, worms, etc., and secures unauthorized access from a private network. The steps required to set up and configure the firewall are listed below:
- Change the default password for a firewall device.
- Disable the remote administration feature.
- Configure port forwarding for specific applications to function correctly, such as an FTP server or a web server.
- Firewall installation on a network with an existing DHCP server can cause errors unless its firewall’s DHCP is disabled.
- Make sure the firewall is configured to robust security policies.
20. How can you prevent CSRF attacks?
Answer: CSRF is referred to as Cross-site Request Forgery, where an attacker tricks a victim into performing actions on their behalf. CSRF attacks can be prevented by using the following ways:
- Employing the latest antivirus software which helps in blocking malicious scripts.
- While authenticating to your banking site or performing any financial transactions on any other website do not browse other sites or open any emails, which helps in executing malicious scripts while being authenticated to a financial site.
- Never save your login/password within your browser for financial transactions.
- Disable scripting in your browser.
As of now, you must have now seen what the questions that are commonly asked look like. They are the right questions for you in this journey and therefore you have to consider yourself lucky because you have found the real deal. You are surely going to walk into the interview with great confidence and you will eventually make it on that big day.
Other Technical Interview Questions you may like to explore for practice
- 15 Data Structure and Algorithm Questions from Java Interviews (read here)
- 50 Linux Interview Questions with answers (Linux questions)
- 20 Java Design Pattern Questions asked on Interviews (see here)
- 15 Java NIO and Networking Interview Questions with Answers (see here)
- 10 Servlet Interview Questions with Answers (see here)
- 10 popular Struts Interview Questions for Java developers (list)
- Top 40 Core Java Phone Interview Questions with Answers (list)
- Top 10 Trick Java Interview Questions and Answers (see here)
- 20 Tibco Rendezvous and EMS Interview Questions (read more)
- 10 Oracle Interview Questions for Java developers (see here)
- Top 10 XSLT Interview Questions with Answers (read more)
- Top 10 EJB Interview Questions and Answers (see here)
- 40 HashMap Interview questions with Answers (hashmap questions)
- 20 Spring Boot Interview Questions with Answers (spring boot questions)
- 10 JDBC Interview Questions for Java Programmers (questions)
- 12 RESTful Web Services Questions from Interviews (read here)
- 10 XML Interview Questions for Java Programmers (read here)
- Top 10 JSP Questions from J2EE Interviews (read here)
- 10 Hibernate Interview Questions for Java EE developers (see here)
- 20 jQuery Interview Questions for Java Web Developers (list)
- 15 Microservice Interview Questions with Answers (Microservice questions)
Thanks for reading this article. If you like these Cyber Security interview
questions and their answers then please share with your friends and
colleagues. If you have any question, feedback or any doubt about these
questions/answers, please drop a comment.
P. S. -
If you are new to Linux and want to learn Linux in depth, both commands
and concepts then I also suggest you to go through these best Cyber Security and Information Security courses to learn Cyber Security in depth.


Q4 - it should be reduces recovery time
ReplyDeleteAh Yes, thanks for pointing out.
DeleteQ4 - it should be reduces recovery time
ReplyDelete